DN42 is an experimental network , where everyone helps everyone. Nobody is going to blame you if you screwed up. You may seek help at DN42's IRC channel , mailing list or the unofficial Telegram group . Since DN42 is a network for experimentation, a lot of relatively inexperienced users also participate in it. Therefore, occasionally an inexperienced user may misconfigure his/her system and impact the whole DN42 network or even shut it down. As a more experienced user, here I will teach new users about some operations that can kill the network and about defense against such misconfigurations that everyone can set up against peers. WARNING: You should not actually perform these operations in DN42. You should focus more on protecting yourself against them....
DN42 Experimental Network: Intro and Registration (Updated 2022-12)
DN42, aka Decentralized Network 42, is a large, decentralized VPN-based network. But unlike other traditional VPNs, DN42 itself doesn't provide any VPN exits, which means it doesn't allow you to bypass Internet censorships or unlock streaming services. On the contrary, the goal of DN42 is to simulate another Internet. It uses much of the technology running on modern Internet backbones (BGP, recursive DNS, etc), and is a great replica of a real network environment. In short, DN42 is: NOT suitable for users only seeking privacy protection or bypassing censorship NOT suitable for users consuming large amounts of bandwidth/data, such as for unlocking streaming services IS suitable for users learning about networking, practicing configuration of servers and routers,...
Setting up DN42 WHOIS Server with Nginx
In my previous post, " Setting up Gopher Site with Nginx ", I mentioned that the Gopher service is a byproduct of my original plan: modifying Nginx into a WHOIS server for DN42. This post will explore into details of that process. The WHOIS Protocol First, we can find a WHOIS server to observe its response. Choose the WHOIS server for .pub domain as an example, and run telnet whois.nic.pub 43 : # Type following line and hit enter lantian.pub # WHOIS server responded with: Domain Name: lantian.pub Registry Domain ID: c69e5ccf9d834900be26f88fddc5c9e4-DONUTS Registrar WHOIS Server: whois.dnspod.cn Registrar URL: https://www.dnspod.cn Updated Date: 2021-01-07T14:09:11Z Creation Date: 2016-10-23T08:36:41Z Registry Expiry Date: 2029-10-23T08:36:41Z Registrar: DNSPod, Inc....
Remove OpenVPN's Stable-privacy IPv6 Addresses
On my VPSes, the TAP network interface created by OpenVPN has a randomly-generated IPv6 address with scope stable-privacy . This address itself is created randomly to prevent tracking users by their IPv6 addresses. But when building a network in DN42, BGP handshakes may originate from this address (rather than your manually assigned link-local address) and fail for mismatching origin/IP. The solution is to configure the TAP interfaces with sysctl, and disable the automatic address generation options. OpenVPN can be configured to run sysctl automatically when creating the interface: # Add to OpenVPN's config file script-security 2 up "/bin/sh -c '/sbin/sysctl -w net.ipv6.conf. $dev .autoconf=0 && /sbin/sysctl -w net.ipv6.conf. $dev .accept_ra=0 && /sbin/sysctl -w net....
Running Anycast DNS with Docker in DN42
2020-03-16 Notes There is an updated scheme compared to this post, see Sharing Network Namespace Among Docker Containers for Bird Anycasting . It is suggested to read only the concept explanations in this post, and use the above scheme instead for deployment. What's Anycast The commonly used routing protocol on Internet, the BGP, works like this: I own an IP range, 172.22.76.104/29, on DN42. With a BGP software like BIRD, I "announce" that my server has access to IP range 172.22.76.104/29. Servers with peering to me will record this message: "Over this path, I can access 172.22.76.104/29 which is 1 step away." These servers continue to announce to others with peering to them: "This server is 1 step away from the source of 172.22.76.104/29." Similarly,...
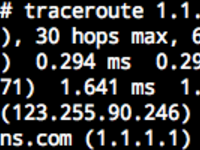
Writing Stories in Traceroute
2020-10-11 Update Now a better way exists that doesn't involve a bunch of Docker containers. Please refer to Writing Stories in Traceroute, Elegantly . Intro Traceroute is one of the popular tools for network inspection. It shows the IP addresses of routers on the route from your computer to a destination server, similar to: Domains are shown on the last 2 hops, which is the IP's reverse DNS record. Reverse DNS records exist as PTR records in the format of 4.3.2.1.in-addr.arpa . For more information, you may refer to Setting IP Reverse Records in DN42 (Chinese Only) . However, PTR records need not be real domains. They can be any string that "looks like" a domain. With this, we can write one sentence on each hop of a Traceroute path to make a story: This story is set up in DN42....
Registering Domain in DN42
DN42, aka Decentralized Network 42, is a large VPN network. Unlike traditional VPNs, DN42 uses a lot of technology involved in Internet backbones (such as BGP) and is a great simulation of a realistic network environment. In a previous post (Chinese only) , I joined DN42 and connected most of my VPSes to it. (The ones left are OpenVZ VPSes without Tun/Tap support.) I knew from the beginning that DN42 has its own domain name system. For example, DN42's wiki ( https://wiki.dn42.us/Home ) can be accessed as https://internal.dn42 in DN42. I didn't register a domain back then since I didn't have time, and I didn't have much knowledge of DN42. I finished the registration this month and would like to share my experience....
